Authored By Anuradha
McAfee Labs has recently observed a new wave of phishing attacks. In this wave, the attacker has been abusing server-parsed HTML (SHTML) files. The SHTML files are commonly associated with web servers redirecting users to malicious, credential-stealing websites or display phishing forms locally within the browser to harvest user-sensitive information.
SHTML Campaign in the field:
Figure 1. shows the geological distribution of McAfee clients who detect malicious SHTML files.
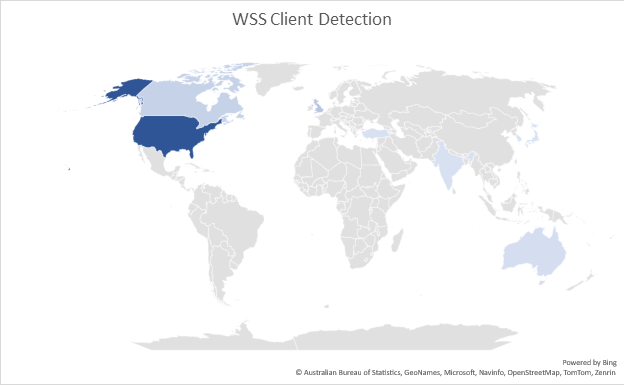
Figure 1. McAfee Client Detection of SHTML
Attackers victimize users by distributing SHTML files as email attachments. The sentiments used in such phishing emails include a payment confirmation, invoice, shipment etc., The email contains a small thread of messages to make the recipient more curious to open the attachment.
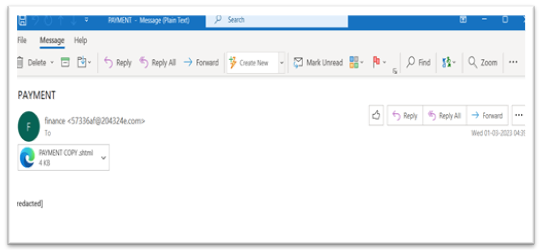
Figure 2. Email with SHTML attachment
Analysis:
When the SHTML attachment is clicked, it opens a blurred fake document with a login page in the browser as shown in Figure 3. To read the document, however, the user must enter his/her credentials. In some cases, the email address is prefilled.
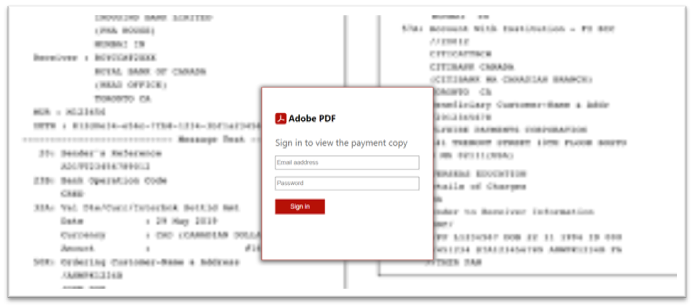
Figure 3. Fake PDF document
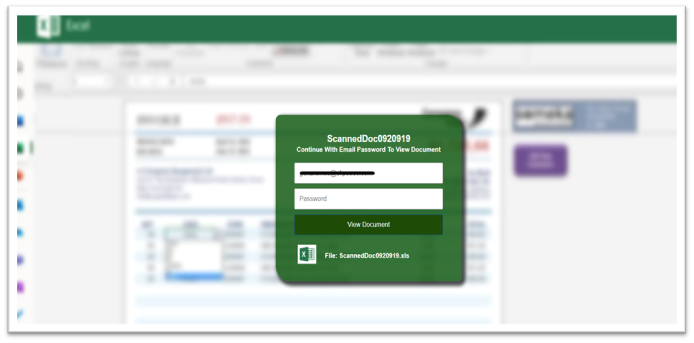
Figure 4. Fake Excel document

Figure 5. Fake DHL Shipping document
Attackers commonly use JavaScript in the SHTML attachments that will be used either to generate the malicious phishing form or to redirect or to hide malicious URLs and behavior.
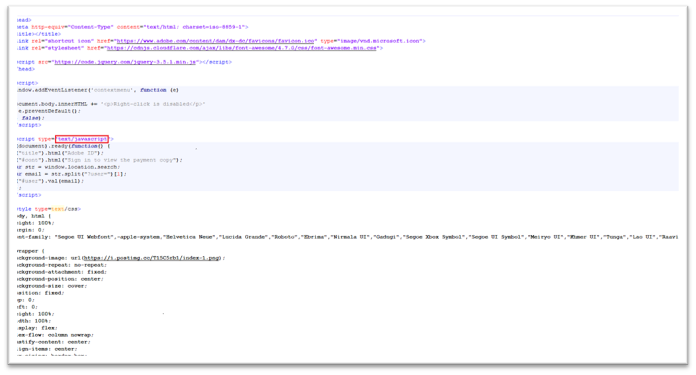
Figure 6. SHTML with JavaScript code
Below is the code snippet that shows how the blurred background image is loaded. The blurred images are taken from legitimate websites such as:
https://isc.sans.edu
https://i.gyazo.com
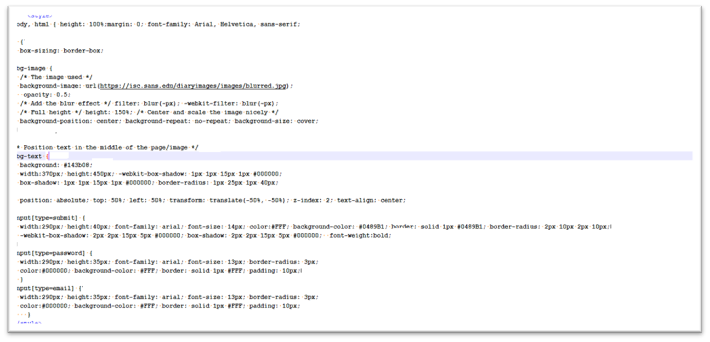
Figure 7. Code to load blurred image
Abusing submission form service:
Phishing attacks abuse static form service providers to steal sensitive user information, such as Formspree and Formspark
Formspree.io is a back-end service that allows developers to easily add forms on their website without writing server-side code, it also handles form processing and storage. It takes HTML form submissions and sends the results to an email address.
The attackers use the formpsree.io URL as an action URL which defines where the form data will be sent. Below Figure 8. shows the code snippet for action URL that works in conjunction with POST method.
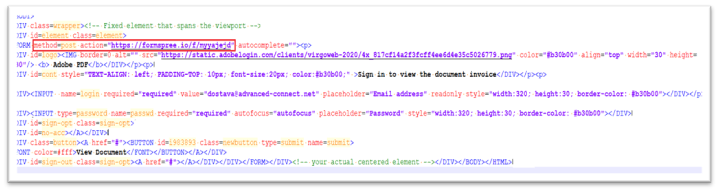
Figure 8. Formspree.io as action URL with POST method
When the user enters the credentials and hits the “submit” button, the data is sent to Formspree.io. Subsequently, Formspree.io forwards the information to the specified email address. Below Figure 9. shows the flow of user submission data from webpage to attacker email address.

Figure 9. Flow of user submission data
Known malicious forms may be blocked, preventing the form submission data from being sent to the attacker. Below Figure 10. shows the Form blocked due to suspected fraudulent activity.
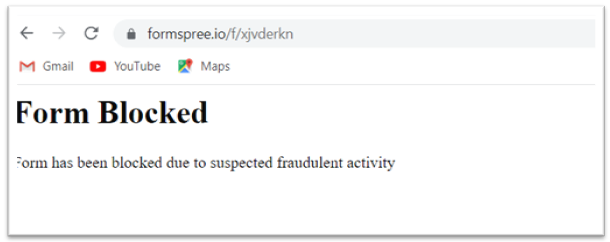
Figure 10. Form Blocked
To prevent the user from recognizing that they’ve just been phished, the attacker redirects the user’s browser to an unrelated error page that is associated to a legitimate website.
Below Figure 11. shows the redirected webpage.
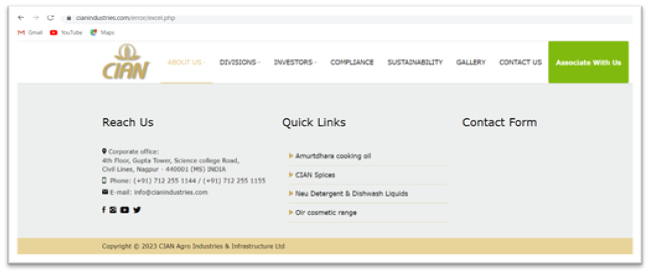
Figure 11. Redirected webpage
To conclude, phishing is a form of social engineering in which attackers trick people into disclosing confidential information or installing malware. It is a widespread and pervasive problem. This blurry image phishing scam uses simple basic HTML and JavaScript code, but it can still be effective. A blurry image is enough to trick many users into believing the email as legitimate. To stay protected, users should keep their system up-to-date and refrain from clicking links and opening SHTML attachments that comes through email from untrusted sources.
IOCs
McAfee customers are protected against this phishing campaign.
|
||||||||||||||||||||
| Type | Value | Product | Detected |
| shtml(Adobe) | 0a072e7443732c7bdb9d1f3fdb9ee27c | Total Protection and LiveSafe | HTML/Phishing.qz |
| shtml(Excel) | 3b215a37c728f65c167941e788935677 | Total Protection and LiveSafe | HTML/Phishing.rb |
| shtml(DHL) | 257c1f7a04c93a44514977ec5027446c | Total Protection and LiveSafe | HTML/Phishing.qz |













